Windows NT Virtual Private Networking
One of the biggest challenges faced by organizations today is that of allowing remote access to corporate networks. The distinction between "Local Area Network" and "Wide Area Network" is being blurred. New and expanding needs of information technology are driving the industry towards open standards and more universal access as "telecommuting" and its associated benefits have become a realistic option for many types of workers. With new technology, sales forces can trust in the availability of instantly available and up-to-date information; corporate decision-makers can access information conveniently, and all users can respond to E-mail from any location. Remote access solutions allow clients to access a company. s network using telecommunications devices, such as modems and other WAN adapters, instead of a network cable. Why is remote access such an important issue today? Apart from the pressures of various industries to move towards truly "distributed computing", many more travelling employees are depending on laptop machines. "Worldwide corporations" are becoming more commonplace and growing pains are becoming the norm as business needs push the limits of information technology. A greater dependence is placed on computing resources as companies compete in a marketplace where real power lies in information . and it. s accessibility. The Internet has provided a ready-to-use worldwide network, waiting to connect remote sites together. Internet Service Providers (ISP. s) are readily available to carry data quickly, and securely, to where it is needed in almost any part of the world. Despite the benefits it can promise, many companies have been reluctant to allow widespread remote access to their corporate LAN. s. Security is, perhaps, the greatest of their concerns. Following closely is the cost and administrative burden of creating modem pools, assigning login permissions and configuring client machines. Fear of trying to keep pace with ever-changing WAN technologies creates potential problems for the future. In the past proprietary hardware-based solutions have often been used in this capacity; however, they often do not address all of the above issues. This paper will discuss the benefits of implementing Windows NT 4.0 Remote Access Server (RAS) as a potential solution for a corporation. s "dial-in" options. With RAS, remote users can share files and printers, access mainframe hosts, interact with databases and synchronize E-Mail and scheduling information. Installing and configuring the server will be discussed first. This will include dial-in options of RAS and the basic assignment of permissions for users who will use these services. Client configuration options will be presented next, including steps involved in installing the necessary software for remote LAN access. Following the configuration information will be a discussion of security issues and information on how Windows NT RAS addresses these potential problems. Finally, exciting new developments in RAS . namely Multi-Link for bandwidth aggregation and Virtual Private Networking via Point-to-Point Tunneling Protocol . will be evaluated.
Virtual Private Networking (VPN) technology can be defined as the usage of an inherently insecure public network for the purpose of securely transferring sensitive information. With the tremendous popularity and ubiquity of the Internet, more and more corporations are finding ways in which to leverage this technology to reduce their data transport costs and ease the implementation of remote access solutions.
Increasing Demand for Remote Access
One of the biggest challenges organizations face today is that of allowing remote access to corporate networks. The distinction between "Local Area Network" and "Wide Area Network" is being blurred. New and expanding needs of information technology are driving the industry towards open standards and more universal access as "telecommuting" and its associated benefits have become a realistic option for many types of workers. Faster, cheaper and more reliable WAN connection methods continue to evolve. With new technology, sales forces can trust in the empowerment of instantly available and up-to-date information; corporate decision-makers can access information conveniently, and all users can respond to E-mail from any location. Remote access solutions allow clients to access a company. s network using telecommunications devices, such as modems and other WAN adapters, instead of a network cable.
Why is remote access such an important issue today? Apart from the pressures of various industries to move towards truly "distributed computing", many more traveling employees are depending on laptops and other portable devices. "Worldwide corporations" are becoming more commonplace and growing pains are becoming the norm as business needs push the limits of information technology. A greater dependence is placed on computing resources as companies compete in a marketplace where real power lies not only in information, but also in its accessibility. The Internet has provided a ready-to-use worldwide network, waiting to connect remote sites together. Internet Service Providers (ISP. s) are readily available to carry data quickly, and securely, to where it is needed in almost any part of the world. This technology is ready to be leveraged to improve business practices and decrease costs today. Users have not only realized the potential of the Internet, but have come to expect location-independent access to their data.
Despite the benefits it can promise, many companies have been reluctant to allow widespread remote access to their corporate LAN. s. Security is, perhaps, the greatest of their concerns. Following closely is the cost and administrative burden of creating modem pools, assigning login permissions and configuring client machines. Fear of trying to keep pace with ever-changing WAN technologies creates potential problems for the future. In the past, proprietary hardware-based solutions have often been used in this capacity; however, they often do not address all of the above issues, and can sometimes present additional problems of their own.
Problems with "Traditional" Remote Access practices
"Remote Access" refers to the use of leased or public lines for the connection of remote users to a Local Area Network (LAN). For the purpose of this paper, "traditional" remote access will be defined as the use of modem pools and on-demand, leased point-to-point connections between users (such as analog phone lines or ISDN lines). Traditional remote access is characterized by the use of "modem banks" on the server side and the use of leased lines that incur charges based on transport traffic as well as time- and distance-based charges. This configuration, though very common for the vast majority of companies, leaves a lot to be desired.
Firstly, implementing a "modem bank" often involves choosing an expensive, proprietary solution from a single vendor. This vendor. s device will support a specified number of "ports" (equal to the number of maximum concurrent connections possible). As business needs grow, the customer must obtain additional hardware from this same vendor. Administration of the modems requires personnel who are familiar with the proprietary standards and operations of a specific device. In some cases, it is necessary for accounts to be created and maintained on the modem bank. More significantly, the usage of each "port" incurs a monthly service charge for leasing the line and a connection charge for long-distance communications. Recently, many remote access administrators have realized the costs associated with upgrading server-side hardware. A prime example is the confusion over 56Kbps analog line modem standards which forced customers to choose between competing and incompatible technologies. As end-users demanded the additional speed, IT departments were forced to replace old modems with more costly new ones on the server side. A similar problem occurs when an employee is provided an ISDN connection . the company must buy hardware at both "ends" of the connection and provision a line for this user. A major technical limitation is seen in the fact that the bandwidth for each traditional point-to-point connection is fixed. That is, if a user dials in at 28.8Kbps, she will be fully occupying that port . whether she is transferring data or not, no other user will be able to utilize the unused bandwidth. This problem can be overlooked for a small number of users, but when many users are concurrently connected, the waste of time and money in connection charges can be tremendous. Overall, the costs, administrative requirements and reliance on proprietary hardware have made "traditional" remote access a difficult technology to implement and maintain.
VPN. s use the Internet (or any other public network) for the transport of data. Client computers (such as laptops or other remote clients) still continue to use modems due to their relatively low cost. Servers, however, use a dedicated Internet WAN link instead of a bank of modems. All data that is transferred between the clients and the server is encrypted. Furthermore, VPN. s are protocol-independent; that is, any type of network protocol can be transferred securely. A PPTP packet can encapsulate any type of data. There are two ways to implement a VPN . via hardware or through software. Additionally, a company may choose to implement a VPN "in-house", or may choose to have this outsource to an Internet Service Provider. All methods will be described in detail later.
The popularity of the Internet, combined with the availability of Virtual Private Networking technology, has brought with it a solution for many of the problems faced with traditional remote access. First and foremost, by leveraging the availability of a free, global, public network, long-distance and other data transport charges can be virtually eliminated. Instead of placing a long-distance call from New York to Los Angeles, an end-user can connect to a local Internet Service Provider (ISP) for a low, fixed monthly rate and connect to any server in the world for which she has an account at no additional cost. This method will pay for itself quickly, even if she does not connect for a long time. The benefits increase dramatically for frequent and international travelers. On the server side, there is no need to maintain expensive, proprietary modem banks. Instead, a single Internet connection (for example, a fractional T1 line) can support many users. This effect is amplified because remote users only use bandwidth while they are transferring data and not while they are idle. It also avoids the need to coordinate with telephone companies to provision the necessary number of analog lines. Although it may incur a slight performance cost on the server and client side, the encryption of all data being transferred over the connections provides additional security. To greatly simplify administration of VPN connectivity, corporations may choose to purchase this service from an ISP who can perform these services transparently. In these ways, VPN technology eliminates many of the problems experienced with traditional remote access.
Among the many advantages of this alternative are:
VPN Implementation: Business Considerations
Although VPN technology may seem far superior to the usage of traditional remote access, there are several business considerations to evaluate before implementing such a solution. The major consideration in this area will concern whether or not there is a need for VPN Technology. Certainly, in cases where remote access is used very rarely (for example, when executives make quarterly trips), or where the majority of remote access is done locally (for a company that has many local offices), several of the advantages of VPN implementation will not be present. Questions to ask include:
Outsourcing vs. In-House VPN Implementation
A major benefit for companies that do not have the time or resources to implement their own VPN is that they can seek this provision from an ISP. By offloading the burden of setting up and configuring servers and WAN connections to a third-party, companies can focus on other business demands. The oftentimes more-capable ISP will be responsible for handling all client installation issues and will keep up with all hardware and software upgrades. Additionally, outsourced VPN. s, if set up by an ISP that has many Points of Presence (POP. s), the usage of this secure, encrypted connection would be transparent to end users.
There are however, several reasons for implementing a VPN in-house. If only a few users will require remote access, it is much cheaper and easier to setup a software-based solution such as Windows NT Remote Access Server (RAS). Also, if greater control over the configuration of the connections and user accounts is required (for example, Jane Doe may only log on between 6:00pm and 12:00 midnight), it would be best to keep these functions in-house.
Best Practice: If ease of implementation is a major plus, VPN. s should be outsourced. If lower costs, more control and/or a small number of users are priorities, then it is best to do this in-house.
VPN Implementation: Technical Issues
Though the need for a Virtual Private Network can be assessed by considering the business case for it, several technical issues must be considered by network administrators and integrators before implementing such a solution.
Though they all utilize the same basic technology, there are multiple different scenarios for VPN implementations:
In most cases, the performance of remote access solutions will be limited by the amount of bandwidth available for clients. This is due to the fact that the fastest WAN links readily available for clients today are relatively slow (usually less than 128Kbps). As the number of simultaneous connections increases, however, there will be some data processing overhead on the receiving server. If a company chooses to manage its own VPN, hardware requirements on the server (or front-end router) may increase. Additionally, the usage of encryption will increase the processing required on both ends of the connection. As processing power will vary greatly between systems, it is recommended that a load test be performed before going "live" with any solution. Load may also be distributed among several remote access servers, if practical.
The reliability of the Internet has often been cited as a major concern regarding the usage of VPN. s. However, the very nature of the Internet protects against many types of failures through redundancy. It is much more likely that dedicated routes will fail than it is for all possible routes on the Internet to be unavailable at the same time. If remote access connectivity is mission-critical, companies will want to have guaranteed levels of availability for their Internet access and will want to implement redundant connections with fail-over capabilities. Performance can also be increased as clients can use their ISP. s connection for general Internet access instead of using up the LAN. s resources.
Best Practice: If it is unknown whether a specific server (computer or router) can handle the anticipated amount of traffic, load testing is important. If remote access is mission-critical, take steps to make connectivity and devices fault tolerant.
Current Standards and Protocols
The basic idea behind VPN. s is that of encapsulation. Any type of packet can be carried within a PPTP packet. The following diagram illustrates the protocol interactions throughout the connection process:
For carrying VPN traffic, there are three major protocol "standards" available on the market today.
Point-to-Point Tunneling Protocol (PPTP): PPTP is a software-based VPN protocol developed by Microsoft for point-to-point connectivity. It is available free as part of Windows 95 (OSR 2.x and above), Windows 98, Windows NT 4.0 and Windows NT 5.0. The use of this protocol is highly recommended for smaller to medium-sized businesses (i.e., less than 50 concurrent connections) as it is freely available in the most common desktop operating systems and is very easy to implement. The method requires no additional setup by an ISP, but will require minor reconfiguration of clients. PPTP is currently limited to 40-bit RSA-DC4 encryption and can only use Microsoft-compatible authentication mechanisms.
Layer 2 Forwarding (L2F): Also devised for client-server remote access scenarios, this standard has been proposed by Cisco and is a hardware router-based protocol. It is available on specific Cisco routers. These devices will accept incoming data from the Internet and route it to the appropriate servers on a LAN. A benefit over PPTP is that stronger encryption schemes may optionally be implemented. Also, various authentication mechanisms (such as RADIUS and TACACS+) are supported by the specification. As L2F is implemented as a hardware-based solution, it may be more scalable than a software implementation of VPN. s and is recommended for medium- to large-sized businesses.
Layer 2 Tunneling Protocol (L2TP): In an effort to consolidate the above two incompatible standards, Cisco and Microsoft are collaborating to create a single protocol for use in VPN. s. It is expected that this technology will be available in all Microsoft Operating Systems in mid- to late-1998, and broad industry support from all major hardware vendors has already been announced. L2TP will be backwards-compatible with both PPTP and L2F.
IP Secure (IPSec): IPSec is being developed by the Internet Engineering Task Force (IETF) as an encrypted protocol for transferring data over the Internet. As of the time of this writing, IPSec had not yet been released as a complete standard for secure Internet tunneling. The design goal for IPSec is for supporting LAN-to-LAN connectivity, and therefore is not a direct competitor for L2TP. IPSec is lacking in support for various secure authentication mechanisms as part of the specification. This major drawback, though being reconsidered, makes it useful for full-time connections.
Best Practice: In evaluating current products, consider the use of L2TP as a major plus for remote users since this will be the new standard for Virtual Private Networking. IPSec will be an important standard for LAN-to-LAN connections. If current solutions do not yet support these standards, ensure the availability of an upgrade path.
A Virtual Private Networking "server" works as an endpoint for outgoing and incoming data communications. This device may either be a computer with appropriate software (e.g., Windows NT Server) or a dedicated hardware router. The equipment may be owned and operated by a company. s IT staff, or by an ISP. In all cases, this device must have at least one serial WAN port with access to the Internet and optionally one port that connects to a LAN. Any computer capable of running Windows NT Server can be configured to work in this capacity. Similarly, hardware from various vendors (Cisco, Shiva, 3Com, Ascend, etc.) can perform the same function. The benefits of hardware routers are greater scalability and increase performance. Windows NT software-based servers, however, have lower initial costs (especially if a server is already available) and provide for easier implementation. Additionally, in the case of Windows NT Server, it is very simple for an administrator to grant remote access to existing workgroup or domain accounts.
Best Practice: For lower costs and ease of implementation and administration, use a software-based VPN router (Such as Microsoft Windows NT Server 4.x or above). If performance and scalability are main priorities, consider dedicated hardware-based solutions.
When considering remote access solutions, security is the foremost issue. Though popular media has scared many IT managers about the inherent insecurity of the Internet, a careful consideration of the facts will show that VPN technology can often be more secure than traditional remote access. Firstly, all data that is sent between the client and server is encrypted. This acts to make the usability of data much more difficult in the unlikely event that it is intercepted in transmission. Additionally, most VPN routers can choose to perform selective packet filtering on the server side to prevent the risk of basic TCP/IP attacks. For example, if only PPTP traffic is allowed through a router, any user that attempts to violate the security of that server must first establish a PPTP connection (i.e., must authenticate on the server). In effect, this server is acting as its own firewall in that it accepts only data from authorized clients. Most implementations of VPN technology also support more advanced authentication mechanisms such as SecureID, RADIUS and other proprietary methods. In order for VPN protocol traffic to travel through a firewall, specific ports must be opened on the firewall. In the case of PPTP, for example, Port 1723 and IP Protocol #47 (GRE) must be allowed to pass. Again, this should not be a major concern since a user must authenticate on the VPN server before sending any data through this port. For interconnecting LAN. s, packet-filtering by IP address is recommended. It is highly recommended that auditing be enabled on the front-end server device to log all activity and to detect unauthorized usage attempts.
Best Practice: In general, VPN connections are more secure than those formed by traditional remote access. It is recommended to configure the VPN server or router to perform packet-filtering for all traffic except that originating via the VPN. For additional security, stronger authentication methods, stronger encryption and auditing may be employed.
Windows-Based Client Configuration
For current Microsoft-based operating systems, configuring a client to dial-in to a Windows NT VPN server is very simple. The client connection sequence is as follows:
If client reconfiguration for existing remote access clients is expected to be difficult (such as in the case of a large number of users or users with non-Microsoft Operating Systems), VPN access can be implemented transparently to the user by using hardware routers or making arrangements with the ISP. If a company allows its users to choose their ISP. s or if there are multiple different ISP. s in use, this solution may not be as feasible.
Best Practice: Client configuration is relatively straight-forward and simple for Microsoft-based operating systems. For non-Microsoft Operating Systems that do not support VPN, consider outsourcing or using hardware-based VPN front-ends. Also, if client configuration is a major issue, consider outsourcing with an ISP.
Handling technology advances in Wide-Area Networking should be a concern for Information Technology administrators. Faster and cheaper solutions will be available shortly, and supporting this new technology will greatly assist a business in allowing its employees to stay connected to mission-critical data. On the client side, Asymmetric Digital Subscriber Line (ADSL), and cable modems are starting to come to market at reasonable prices. On the server-side, high-bandwidth connections such as T1, Frame Relay and ATM continue to become more affordable. Clearly, new technologies such as Voice-over-IP and full-duplex video conferencing are on the horizon. A major benefit of the implementation of a VPN will be that clients can freely upgrade to whatever bandwidth they find to be practical. All required hardware and software support will be provided by the ISP. To support increased bandwidth demands on the server side, upgrading modem devices will not be an issue as the replacement or upgrade of a single router is all that will be needed.
Figure 4. Reduction in Total Number of Connections needed to connect 5 sites.
Windows NT VPN Setup
Microsoft provides free Virtual Private Networking software and protocols with the Remote Access Service (RAS) and Dial-Up Networking (DUN) components of all of its current operating systems. Windows NT Server 4.0 can easily be configured to be a VPN gateway and may allow up to 256 concurrent connections. Windows NT Workstation 4.0 and Windows 95 are capable of being VPN clients.. Microsoft has committed to improving support of these standards in future operating systems. In this section the configuration and implementation of a Windows NT VPN will be discussed. The goal is to provide the reader with the information necessary to quickly and easily implement a securely tunneled data channel over the Internet.
The following discussion will assume that a medium-sized company has 500 employees. Of these, 50 are frequent travelers and will often require remote access. Based on these figures, it is estimated that at any given time there will be no more than 20 concurrent connections to the LAN from remote sites. The current corporate standard for traveling users is Windows NT Workstation 4.0, although several laptops are also using Windows 95. The company. s LAN has a single T1 (1.544 Mbps) connection to the Internet that is usually severely underutilized as only certain individuals have Internet access. Recently, it has been noticed that remote access costs are far too high, especially in the area of long-distance costs and server-side hardware. As the company is growing rapidly, the CIO wishes to quickly implement an inexpensive and secure solution. She has evaluated many different options and believes that the software included in Windows NT will meet the required criteria.
The Remote Access Service (RAS) runs on a Windows NT 4.0 Server. The company has decided to utilize an existing Internet connection (a T1 line) to allow remote users to connect to the LAN. In order to accomplish this, it is decided that the RAS server should be placed outside the firewall. The server will allow for receiving connections and will pass authentication information to the Primary Domain Controller. For security purposes, the server will enable packet-filtering, and the audit long will be enabled. The RAS service and PPTP (a protocol) must be installed first. Instead of specifying a modem attached to a COM port as a "dial-in" device, the server uses a "VPN Port". This VPN port is a logical construct that is used to create the communications tunnel. Although NT Server can support up to 256 simultaneous VPN connections (hardware- and bandwidth-permitting), the company will implement 20 ports as this is the maximum number of simultaneous connections expected. Users will then be granted specific permissions to have dial-in abilities.
Installation of the service involves entering the Network options in Control Panel to add the service. Administrator access is required to add this service. The Remote Access Service configuration box will allow enabling the available hardware devices specified in hardware configuration. Any number of available devices can be added to RAS. Each device must be configured to allow either dial-in, dial-out or both. Finally, the acceptable protocols to be enabled for each port must be chosen. To activate the configuration, the server must be restarted.
Point-to-Point Tunneling Protocol (PPTP)
Windows NT RAS can take advantage of the Internet as a medium for connecting remote clients to corporate networks. PPTP provides a secure way to encapsulate PPP data in IP packets. Since it carries PPP, it can use multiple protocols and can transmit any kind of packet over IP. Instead of using a direct ISDN or modem connection, users can utilize any connection to the Internet for transport.
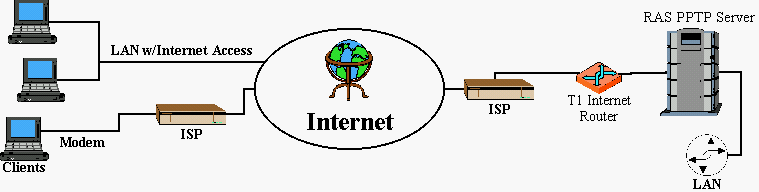
PPTP can currently be implemented in one of two ways. The first is a hardware-based solution that takes advantages of services offered by Internet Service Providers. All installation, configuration and management of the secure connection is provided by the ISP. s hardware. Several hardware manufacturers . including 3Com, Ascend and U. S. Robotics . support this standard. This method has the benefit of being client-independent . As long as the server and client can establish a connection, encryption can be provided by the hardware. The below diagram shows this setup:
An outsourced dial-up network using PPTP
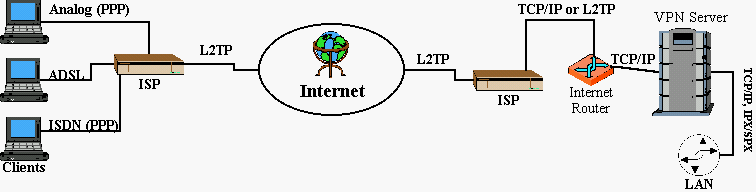
Alternatively, if connecting Windows NT 4.0, Windows 95 and other operating systems that support PPTP, no additional support from the ISP is required since the client and the server can handle all encryption via the operating system.
RAS client dialing into an ISP
For security, RAS use RSA RC4 40-bit encryption for transferring data. For authentication, both PAP and CHAP encryption may be used (see Security for a description of these methods). In effect, this allows the Internet to act as a secure network backbone that can not only support TCP/IP, but also can transmit IPX and NetBEUI. Additional security for PPTP can be configured by using Windows NT. s built-in packet filtering. When enabled, this effectively disables all protocols except PPTP for the specified port. This is important for multi-homed machines because it can limit all incoming traffic to that server to authenticated, secure PPTP connections.
Virtual Private Networking on Windows NT has recently been expanded to allow server-to-server connections. Functionality is provided in the Windows NT Server Routing Upgrade (formerly code-named "Steelhead"), available free from Microsoft. This effectively allows distributed corporate networks to use the Internet as a virtual backbone for remote sites. The main advantage is a dramatic decrease in the costs associated with provisioning WAN leased lines. Since there is already a global infrastructure available for transporting data securely, there is no longer a need for companies to lease a line to connect two or more remote locations.
Windows NT 4.0 and Windows 95 are the only operating systems that currently support PPTP technology. Windows 95 does not include a PPTP server service and requires the recently-release free Dial-Up Network 1.3 Upgrade from Microsoft in order to connect to PPTP servers. Therefore, software-based PPTP implementations are recommended for Microsoft-O/S based corporations. In general, PPTP is configured very much like other Dial-Up Networking connections. The main difference is that an IP address is entered instead of a phone number for the connection information. The client connection sequence is as follows:
The client configuration procedure is similar for both Windows NT and Windows 95. On both operating systems, the "Point-to-Point Tunneling Protocol" must be installed and bound to the dial-out device. Additionally, a Dial-Up Networking connection must be created. On Windows 95, this connection will specify the remote IP address to which to connect. The Dial-Up Adapter will be a "VPN Port" (a logical device used by PPTP). On Windows NT, after installing the PPTP protocol, a "Virtual Port" is created (by default named "RASPPTPVPN1"). This . port. acts exactly like any other dial-out device and must be selected as the adapter for dial-out in the new Dial-Up Networking connection.
In order to allow PPTP connections, the Windows NT Server must have the "Point-to-Point Tunneling Protocol" installed. When installing the protocol, the number of "Virtual Private Networks" must be defined. This number refers to the actual maximum number of connections that will be allowed to the RAS server via the Internet. The maximum number of connections supported is 256. Each of these . Virtual Ports. must then be configured in the RAS Administrator as available dial-in ports.
In order to allow PPTP packets into a network, all routers along the virtual circuit must allow the passage of control information on Port 1723 and allow data transfer via Protocol #47 (Generic Routing Encapsulation) to be passed. This will not be a concern for most implementations as most ISP. s forward these packets by default. Some packet-filtering configurations may restrict data throughput on this port, and therefore may need to be reconfigured. The same concern is valid for hardware implementations of PPTP . that is, if any router along the way restricts these packets, sessions cannot be established.
Following a reboot of the server, several new options will be available. The Remote Access Administrator is part of the "Administrative Tools" program group and can be used to start and stop the RAS service, view the number of current connections, show which ports are available for dial-in and dial-out, and to grant or revoke remote login permissions for users. To grant remote dial-in permissions to users, the Remote Access Administrator can be used. A list of users specified on the server will be shown, along with a check box to grant login permissions. From this screen, call-back verification options can also be set (see Security for further information). The same permissions and call-back options can also be controlled via the User Manager application.
RAS can be configured to let clients access only the resources on the RAS server itself, or it may allow access to the entire network (assuming the client has appropriate permissions). After the RAS service has been started, the server will be ready to accept remote connections from any of the designated dial-in ports.
Selecting from the three available protocols is usually fairly straight-forward and are based on the needs of the client.
Whether the client can access only the remote server or the entire network can be determined in the options for each protocol.
Server Performance Monitoring & Tuning
In general, RAS can be a very scalable solution. The number of acceptable simultaneous connections can be increased by upgrading a servers hardware configuration. Even in cases where the current hardware of one RAS server is pushed to its limits, additional servers can be easily added to share the load. In order to determine the necessary hardware for achieving a given level of performance, monitoring current statistics is important. Installing the Remote Access Service makes . RAS Port. and . RAS Total. counters available in Performance Monitor. The RAS Port counters monitor performance of a single RAS port, and the RAS Total counters monitor all of the ports as a single unit. Among the available counters for both objects are:
Additionally, the basic performance parameters for a server should be considered. A consistently high CPU utilization may indicate that either the remote access hardware is putting a heavy burden on the processor, or that the server is running too many different services to perform acceptably. A consistently large number of page faults per second is indicative of a need for more RAM on the server. Finally, a very high number of interrupts per second could indicate a possible hardware failure.
The Remote Access Administrator will show which ports are in use and which ports are available. If all ports are often in use, it will probably be necessary to increase the number of ports or to disconnect idle users periodically. If some ports are displayed as not available, this may indicate a configuration error or a hardware failure that needs attention. Additionally, Remote Access Administrator can be used to view the current state of all RAS servers in a domain. Using these monitoring methods can greatly reduce the amount of . trail & error. required to reach a given level of performance.
Similar to server installation, clients will have to install the Point-to-Point Tunneling Protocol (PPTP), and Dial-Up Networking. First, some sort of connection that allows for Internet access must be enabled. This may be via a network adapter (in the case that a client is connected to a LAN), or via a WAN adapter (most commonly a standard analog modem). Once Internet access is established, a second connection must be made. This connection will use a "VPN Port" (as above) as a dial-out device. Instead of a phone number, this port will use the IP address of the remote server. The user must connect to the Internet initially. After connection is made, she must then "dial" the remote server and authenticate before being able to access remote resources. Furthermore, once it is setup, clients can setup "demand dialing" for automatically connecting to remote servers. They will no longer need to be aware of which resources are available via their ISP and which are available on a remote network, as the client. s machine will automatically connect via the appropriate method when data is requested.
For most current desktop and workstation configurations, the limiting factor in throughput will be the WAN adapter and, in the case of analog lines used by modems, the quality of the line. It is unlikely that CPU performance, serial interface rates and memory limitations will cause any appreciable decrease in achieve maximum throughput. In addition to monitoring the types of performance discussed earlier (see Server Configuration), the Windows NT Dial-Up Networking Monitor (Figure 1) can provide additional information about the connection speed and the quality of the line. Similar in-depth information, can be obtained by the Windows 95 System Monitor application (Figure 2). System Monitor includes a counter for Dial-Up Adapters and also a Counter for individual modem devices (as long as the "Record a log file" option is enabled. Both of these utilities can show if the line quality is acceptable and if the server is providing adequate throughput.
This section will discuss the various security considerations for implementing RAS as a solution for remote access. Security issues related to Point-to-Point Tunneling Protocol (PPTP) will be discussed in a later section.
Since WAN connections are not normally owned by a company, it is very important to protect all data travelling on these links. Passwords must be protected, even if they are intercepted during transmission by an intruder. To ensure that remote logins are at least as secure as logins over the Local Area Network, various options are available for sending passwords in encoded form. This reduces the likelihood of an intruder decoding passwords, even if they are intercepted from the connection. Authentication mechanisms include the following:
Which authentication protocol is used is based on the capabilities of the client. CHAP provides the best level of security and is used as the default encryption method, whenever possible, by RAS. This method will use the government. s Data Encryption Standard (DES) which uses a 64-bit encryption key algorithm. MD5 can be used by RAS for dial-out, but is not included as part of RAS server for dial-in. If none of the above encryption methods are compatible, RAS can try to use clear-text authentication (PAP). This feature should be disabled to provide for the best possible security.
In order to gain access to network resources via a Windows NT RAS Server, a user must have appropriate permissions to login to the server remotely. If the server is in a workgroup, the user must have a valid account and password. For allowing dial-in access to the entire network, a domain setup is highly recommended. Among the advantages of this type of network are:
If the user is logging into a Windows NT Domain Controller (either Primary or Backup), the user must also have domain login permissions. After authentication, the domain user will have access to all resources that would be available over the LAN (had the user logged in over the network).
Call-back verification can add an extra level of security. Windows NT RAS can be configured to force users to enter the phone number from which they are calling as part of the login procedure and have the Server call them back to establish a connection. There are three options available for this feature: 1) Always return the call to a preset number; 2) Allow the caller to specify a phone number from which he is calling; and, 3) Allow no call-backs. Call-backs occur after a user has been authenticated, but before network access is granted. Therefore, no unauthorized callers may request callbacks from the RAS server. Connections can be restricted so that the must originate from a known phone number (for example, from the user. s home). This provides the benefit of ensuring that the client is calling from a trusted location and can help reduce the risk of outside hacking attempts. Additionally, call-backs can be used to shift the burden of long distance charges incurred by the remote user to the corporation directly.
The same security features used by Windows NT are applicable to remote connections. For example, account lockout after a specific number of unsuccessful login attempts can be enabled. Minimum and maximum password age and password uniqueness can also be enabled. Even after logging in, a user must have explicit permissions to access files, directories and printers. As already discussed, the benefits of domain security include the ease of administration and granting of permissions. For example, Domain Administrations can disconnect a single user logged-in remote to the domain from any RAS-enabled server regardless of which server was used to login.
Finally, for an additional level of security, several third-party products (which will not be discussed here) can be used to authenticate users before they can attempt a RAS connection. Some of these methods require a user to swipe a pass-card before connecting to the remote server. In order for these devices to work, a modification of the default Windows NT RAS scripts is usually required.
By default, PPTP uses RSA-DC4, 40-bit encryption for the transfer of data. For authentication, one of several methods is available. Windows NT Challenge-Handshake Authentication Protocol (CHAP) is recommended, as this method does not actually send the password over the network. Instead, it sends a string determined by a one-way function that is made up of the client machine name and the current user account. Though this is the most secure method of authentication, its drawback is that it is limited in use to clients that support this protocol . namely Windows 95/98 or Windows NT. For all other types of clients, Password Authentication Protocol (PAP) is available. Though this method does send a clear text password over the connection, it is the most compatible standard available.
Auditing can provide a very powerful method for viewing user activity on the server and the network. To enable auditing in Windows NT, the User Manager application can be used to set the system-level auditing policy. Here, tracking various events such as logon successes and failures and file access attempts can be enabled.
A high number of logon failures may indicate failed hacking attempts. Audit data is stored in the Windows NT Event Viewer under the . Security. log and can be viewed by any user with appropriate permissions. The audit log may also provide useful information about which users are frequently using remote access services and when they are calling.
The following table lists the reduction in implementation costs of both the "traditional" solution and the solution using Windows NT PPTP:
Note: The following calculations do not include these items as they are similar in both cases: Internet connectivity (line and adapter cost), Server hardware, Installation and setup, Modem costs for clients
|
Item |
"Traditional" RAS |
PPTP |
|
Phone Line Group Setup (20 lines @ $20/each) |
$400 |
N/A |
|
Modem Bank (20 ports @ $100/each) |
$2,000 |
N/A |
|
Total (one-time cost) |
$2,400 |
$0 |
|
Item |
"Traditional" RAS |
PPTP |
|
Phone Line Maintenance (20 lines @ $15/month/line) |
$300 |
N/A |
|
ISP Charges for Internet Access (50 total users) |
N/A |
$1,000 ($20 per user, unlimited use) |
|
Long distance charges1 |
$1,404 |
N/A (assumed local dialing) |
|
Total (per month) |
$1,704 |
$1,000 |
1
Based on the assumption that, on average, each user will spend 12 hours per month connected to the network, the average number of connected users at any given time will be 15, and the cost for long-distance charges averages $.13 per minute.As users are searching for better ways to remain connected to information resources from anywhere in the world, more network administrators are realizing the true potential of the Internet. And, as more technology users have come to expect location-independent access to data, better ways to connect them have been developed. Many businesses are struggling to remain competitive in information technology as their employees demand a more powerful gateway to their office tools. Virtual Private Networking provides solutions for many of the problems hindering the adoption of wide-spread remote access implementation . namely, cost, security and technical issues involved in implementation and maintenance. In evaluating the business and technical issues involved, it has become quite clear that there is a much better solution available today. Virtual Private Networking frees corporate IT departments from being locked into proprietary, hardware-based remote access solutions. It allows for capitalizing on the presence of a freely available public network as a secure channel for transmitting sensitive information. In so doing, it provides a cost-effective way of connecting a potentially unlimited number of users to their corporate networks. Furthermore, it does so cheaply, securely and effectively. Virtual Private Networking can help deliver information with those who need it . independent of their location. After all, the true power of information cannot be realized without one prerequisite . its accessibility.